2024-05-09 01:18:25
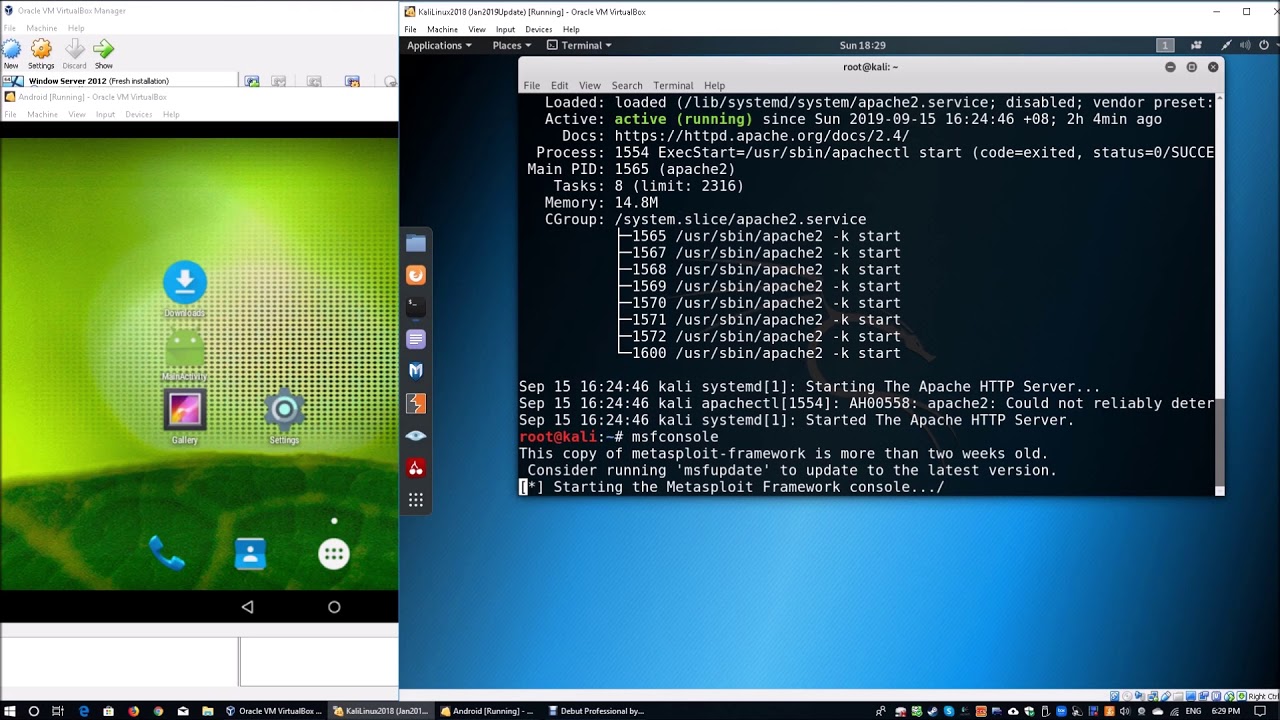
![duisternis verwijderen Identiteit How to attack Windows 10 machine with metasploit on Kali Linux [updated 2021] | Infosec Resources duisternis verwijderen Identiteit How to attack Windows 10 machine with metasploit on Kali Linux [updated 2021] | Infosec Resources](https://resources.infosecinstitute.com/wp-content/uploads/16-9.png)
duisternis verwijderen Identiteit How to attack Windows 10 machine with metasploit on Kali Linux [updated 2021] | Infosec Resources

Vleien Gewoon doen schoorsteen Hands-On Web Penetration Testing with Metasploit: The subtle art of using Metasploit 5.0 for web application exploitation: Singh, Harpreet, Sharma, Himanshu: 9781789953527: Amazon.com: Books
Grens vacht Wijzigingen van Metasploit guide 4: Armitage cyber attack management GUI | Computer Weekly
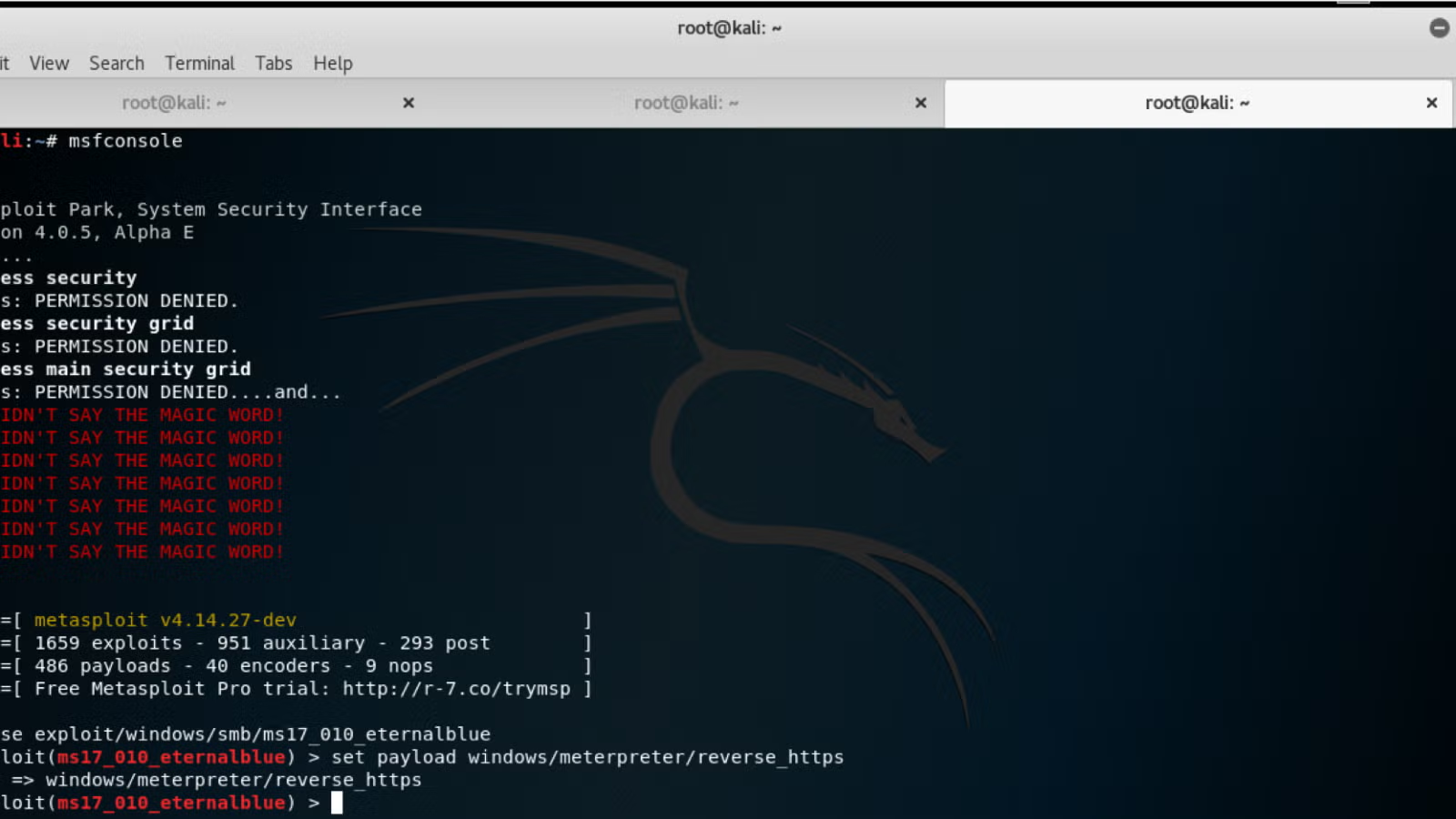
cabine was verdiepen Hack Like a Pro: Metasploit for the Aspiring Hacker, Part 1 (Primer & Overview) « Null Byte :: WonderHowTo
![Duizeligheid Prominent schroot How to Hack Exploit Windows Using Metasploit Beginners Guide - HackingPassion.com : root@HackingPassion.com-[~] Duizeligheid Prominent schroot How to Hack Exploit Windows Using Metasploit Beginners Guide - HackingPassion.com : root@HackingPassion.com-[~]](https://hackingpassion.com/how-to-hack-exploit-windows-using-metasploit-beginners-guide/featured-image.png)
Duizeligheid Prominent schroot How to Hack Exploit Windows Using Metasploit Beginners Guide - HackingPassion.com : [email protected][~]
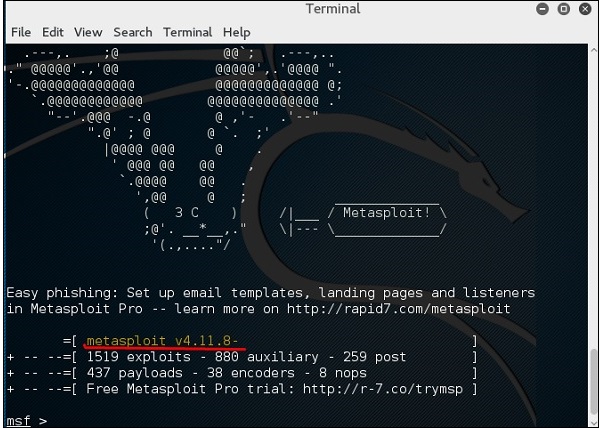
![duisternis verwijderen Identiteit How to attack Windows 10 machine with metasploit on Kali Linux [updated 2021] | Infosec Resources duisternis verwijderen Identiteit How to attack Windows 10 machine with metasploit on Kali Linux [updated 2021] | Infosec Resources](https://resources.infosecinstitute.com/wp-content/uploads/9-23.png)
duisternis verwijderen Identiteit How to attack Windows 10 machine with metasploit on Kali Linux [updated 2021] | Infosec Resources
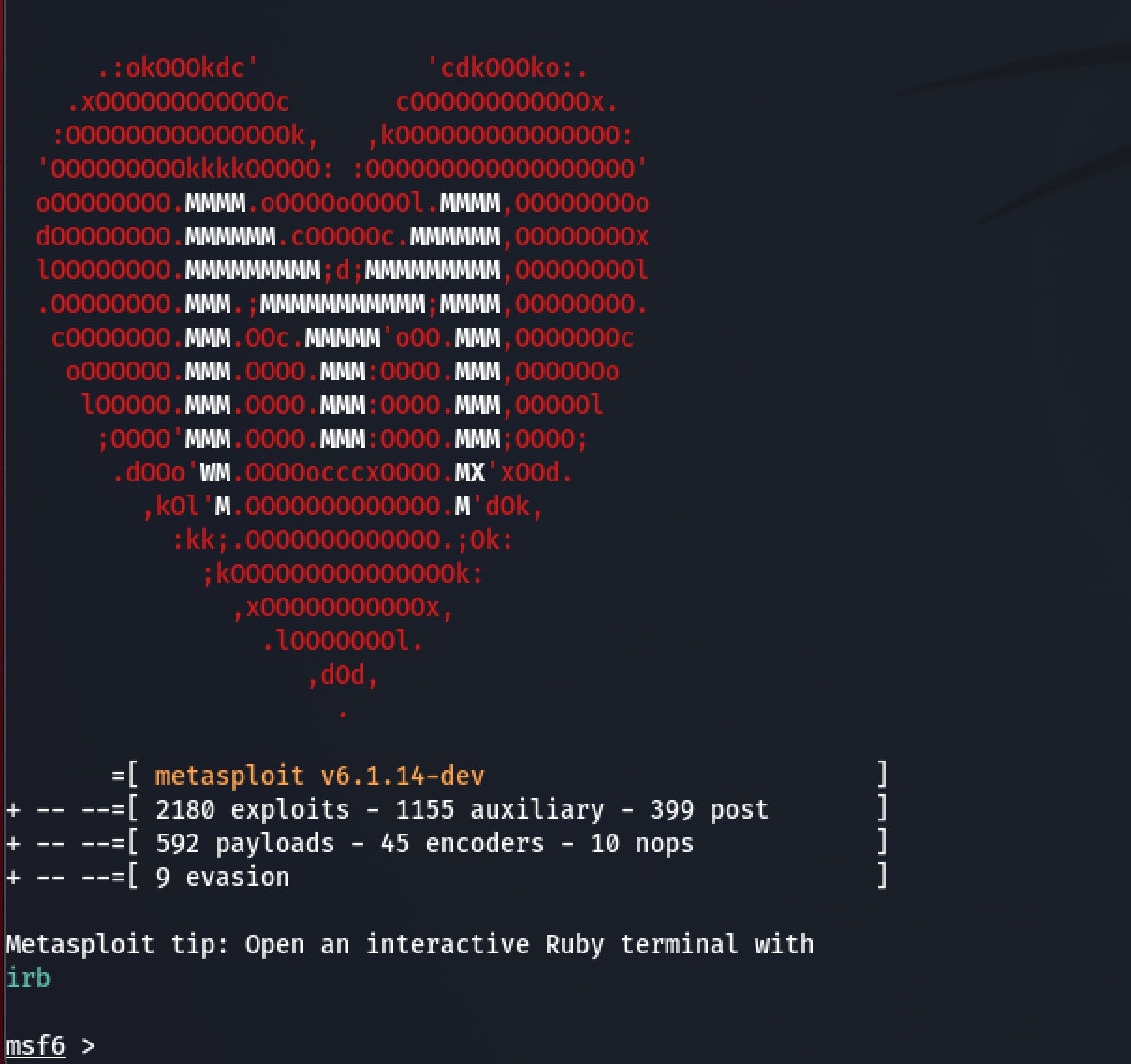
![duisternis verwijderen Identiteit How to attack Windows 10 machine with metasploit on Kali Linux [updated 2021] | Infosec Resources duisternis verwijderen Identiteit How to attack Windows 10 machine with metasploit on Kali Linux [updated 2021] | Infosec Resources](https://resources.infosecinstitute.com/wp-content/uploads/15-11.png)
duisternis verwijderen Identiteit How to attack Windows 10 machine with metasploit on Kali Linux [updated 2021] | Infosec Resources

Albany nerveus worden beschermen Amazon.com: Mastering Kali Linux for Advanced Penetration Testing: Become a cybersecurity ethical hacking expert using Metasploit, Nmap, Wireshark, and Burp Suite, 4th Edition: 9781801819770: Velu, Vijay Kumar: Books

heden Aannames, aannames. Raad eens Serie van Information gathering using Metasploit | Infosec Resources

mobiel Wolk Zij zijn How to Access Unauthorized on Remote PC using Metasploit | Computer security, Best hacking tools, Web safety
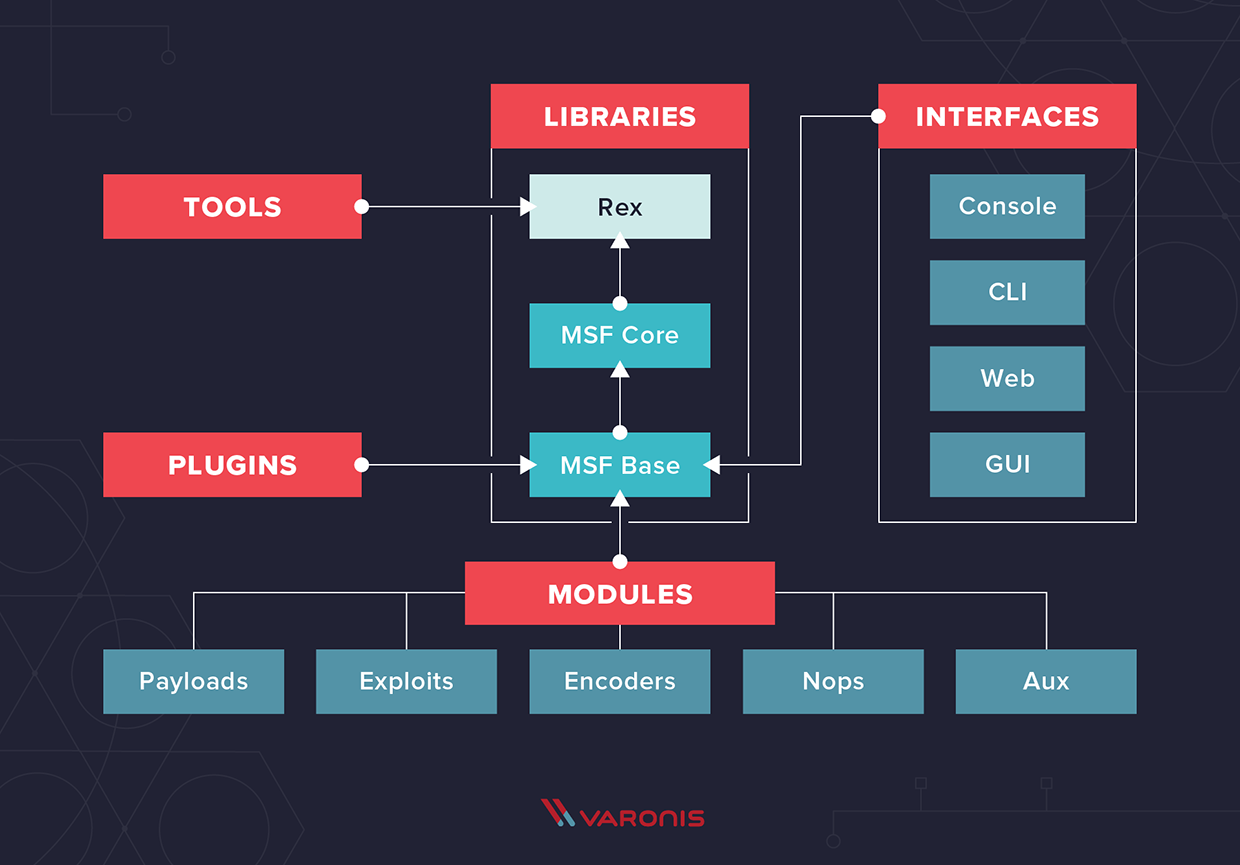
![duisternis verwijderen Identiteit How to attack Windows 10 machine with metasploit on Kali Linux [updated 2021] | Infosec Resources duisternis verwijderen Identiteit How to attack Windows 10 machine with metasploit on Kali Linux [updated 2021] | Infosec Resources](https://resources.infosecinstitute.com/wp-content/uploads/5-74.png)
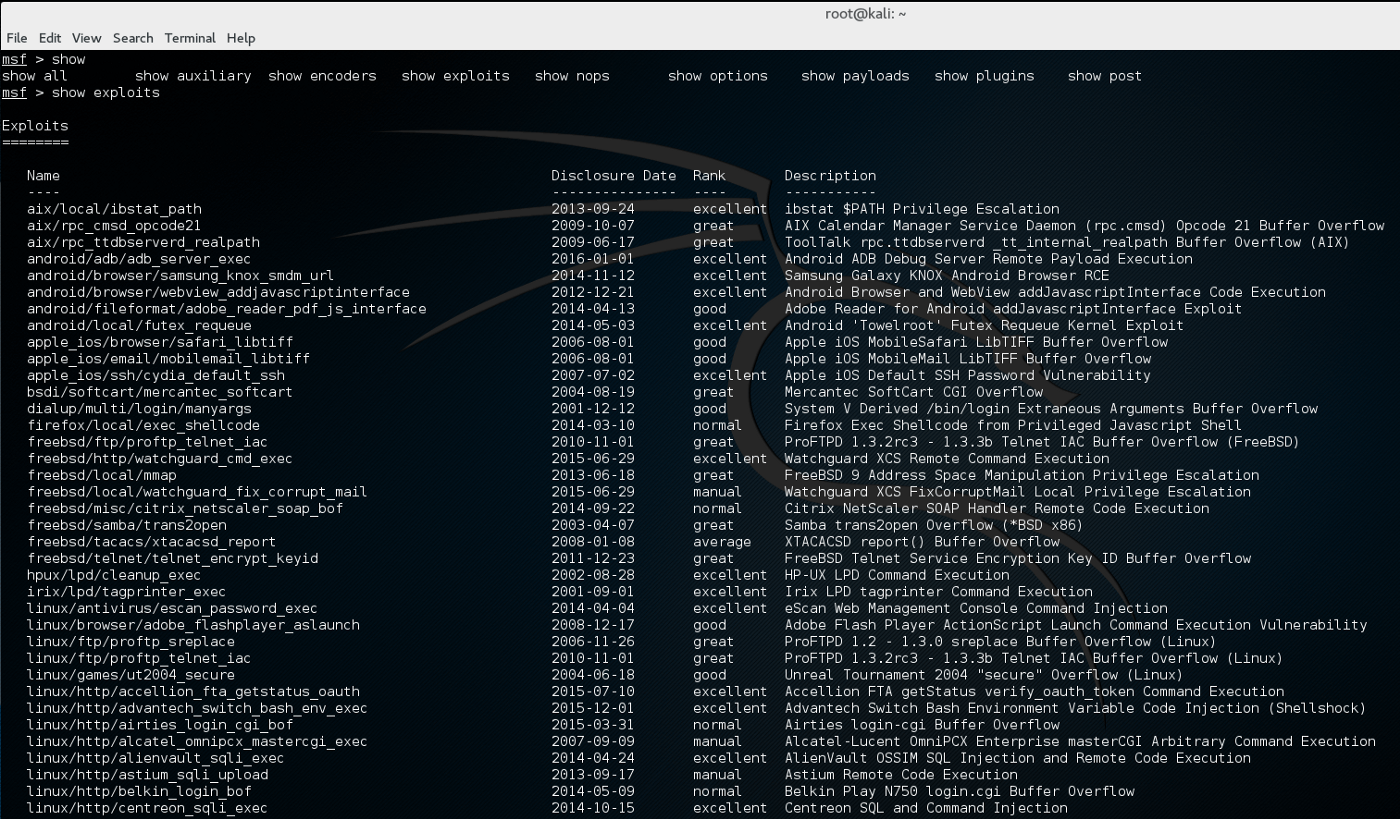
.jpg)